DDoS Attack: Types, Impact, Prevention & Examples
In the age of the internet, cyber threats are an ever-present concern, and DDoS attacks (Distributed Denial of Service attacks) rank among the most disruptive and challenging to combat. These attacks aim to overwhelm a target system, server, or network with excessive traffic, causing a denial of service for legitimate users.
This article dives deep into what DDoS attacks are, how they work, their types, the impact they have, and effective prevention strategies to safeguard your online assets.
What is a DDoS Attack?
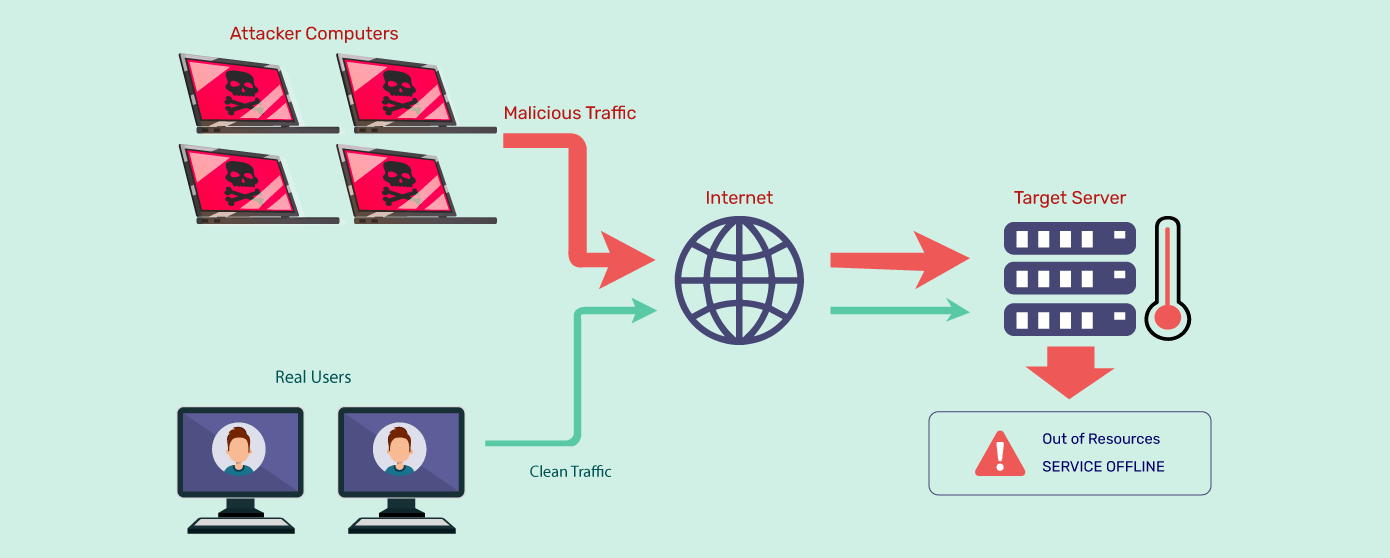
A DDoS attack is a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of internet traffic. Unlike a DoS (Denial of Service) attack, which originates from a single source, DDoS attacks involve multiple compromised systems—often forming a botnet—to amplify the scale of the attack.
How Does a DDoS Attack Work?
DDoS attacks exploit vulnerabilities in the target system or the communication protocols it uses. Here’s a simplified breakdown:
- Infection of Devices: Attackers compromise numerous devices (e.g., computers, IoT devices) through malware to create a botnet.
- Command and Control: The attacker controls the botnet remotely, often using a command-and-control server.
- Initiation of Attack: The botnet sends an overwhelming amount of traffic to the target.
- Resource Exhaustion: The target's server or network becomes overloaded, resulting in slow responses or complete unavailability.
Types of DDoS Attacks
DDoS attacks can be categorized based on the methods they use to overwhelm the target:
1. Volumetric Attacks
- Objective: Consume the target's bandwidth by sending a massive amount of traffic.
- Methods: UDP floods, ICMP floods, or amplification attacks (e.g., DNS amplification).
- Example: Sending large amounts of spoofed DNS responses to exhaust the target’s resources.
2. Protocol Attacks
- Objective: Exploit weaknesses in network protocols to overwhelm resources.
- Methods: SYN floods, Ping of Death, or fragmented packet attacks.
- Example: Sending incomplete handshake requests to exhaust server resources.
3. Application Layer Attacks
- Objective: Target specific applications, such as web servers, to exhaust resources.
- Methods: HTTP floods, Slowloris attacks.
- Example: Sending continuous HTTP requests to a website to consume server resources.
Impact of DDoS Attacks
DDoS attacks can have far-reaching consequences, affecting businesses, organizations, and individuals:
1. Downtime
- Websites and online services become unavailable, causing inconvenience to users and loss of revenue.
2. Financial Loss
- Prolonged downtime can lead to significant revenue losses, especially for e-commerce businesses.
- Companies may incur additional costs for mitigation, recovery, and prevention.
3. Reputation Damage
- Users may lose trust in an organization's ability to secure its online assets.
- Negative publicity can harm a company’s image.
4. Operational Disruption
- Internal operations relying on affected systems may come to a standstill.
5. Legal and Compliance Issues
- Organizations may face legal repercussions for failing to secure user data or comply with cybersecurity regulations.
Real-World Examples of DDoS Attacks
1. GitHub (2018)
- GitHub faced one of the largest DDoS attacks, peaking at 1.35 Tbps, through a Memcached amplification attack.
- The attack disrupted the platform but was mitigated within minutes.
2. Dyn (2016)
- A DDoS attack on the DNS provider Dyn affected major platforms like Twitter, Netflix, and Reddit.
- The attack leveraged a botnet of IoT devices, highlighting vulnerabilities in connected devices.
3. Amazon Web Services (AWS) (2020)
- AWS experienced a massive 2.3 Tbps DDoS attack, which it successfully mitigated.
- This demonstrated the increasing scale of modern DDoS attacks.
How to Detect a DDoS Attack
Early detection is crucial for mitigating the impact of a DDoS attack. Here are common signs:
- Slow Network Performance: Websites or services take longer than usual to load.
- Unavailability: Frequent disconnections or inability to access resources.
- Unusual Traffic Patterns: A sudden spike in traffic from multiple locations or IP addresses.
- Overloaded Servers: Server resources like CPU and memory are maxed out unexpectedly.
- Error Messages: Users encounter errors like “503 Service Unavailable.”
Prevention and Mitigation Strategies for DDoS Attacks
1. Use a Content Delivery Network (CDN)
- CDNs distribute traffic across multiple servers, reducing the impact of an attack.
- Examples: Cloudflare, Akamai.
2. Implement a Web Application Firewall (WAF)
- WAFs filter and block malicious traffic targeting applications.
- They are effective against application-layer attacks.
3. Enable Rate Limiting
- Limit the number of requests from a single IP address to prevent flooding.
4. Deploy Anti-DDoS Services
- Use specialized DDoS protection services offered by providers like AWS Shield, Google Cloud Armor, or Arbor Networks.
5. Monitor Traffic Patterns
- Regularly analyze network traffic to identify anomalies.
- Tools like Wireshark or SolarWinds can help.
6. Set Up Redundant Infrastructure
- Distribute resources across multiple servers and data centers to ensure resilience.
7. Secure IoT Devices
- Regularly update firmware and use strong authentication to prevent IoT devices from being compromised.
8. Conduct Penetration Testing
- Test your systems to identify vulnerabilities that attackers could exploit.
Legal and Ethical Considerations
Launching or participating in a DDoS attack is illegal in most countries and punishable by law. Organizations must ensure compliance with cybersecurity regulations and respond to attacks ethically by collaborating with law enforcement and cybersecurity firms.
Future Trends in DDoS Attacks
As technology evolves, so do DDoS attack techniques. Here are some emerging trends:
- IoT-Based Botnets
- The rise of IoT devices increases the potential for larger botnets.
- AI and Machine Learning
- Attackers may use AI to automate and enhance the sophistication of attacks.
- Advanced Mitigation Techniques
- AI-driven defense mechanisms are being developed to detect and mitigate attacks in real-time.
- Targeted Attacks
- Future DDoS attacks may focus more on specific industries, such as healthcare or finance.
Summary
A DDoS attack is one of the most challenging cybersecurity threats, capable of causing significant damage to businesses and individuals alike. Understanding how these attacks work, their types, and their impact is crucial for defending against them. By adopting proactive measures like deploying CDNs, WAFs, and monitoring tools, you can reduce your vulnerability and protect your online assets.